Setup SAML SSO
Configuration on Identity Provider
The following is a list of IdPs with links to their respective guides explaining the integration process: While we only have official guides for the above providers, the overall process remains quite similar while integrating with any other popular IdP (such as ADFS, PingFederate, etc.) via a SAML 2.0 based connector.Configuration on DeepSource Enterprise Cloud
Before you can connect an Identity Provider (IdP) to your DeepSource team, you need to first verify the ownership of your organization’s email domain. This should be the domain name of your user’s email addresses used for signing into DeepSource.Request domain verification
- Go to https://app.deepsource.com.
- Select the team from the account switcher on the top-left.
- Click on the Settings tab on the nav bar and then click on Security from the left side bar.
- Under Domain name, enter the domain name you want to verify on DeepSource.
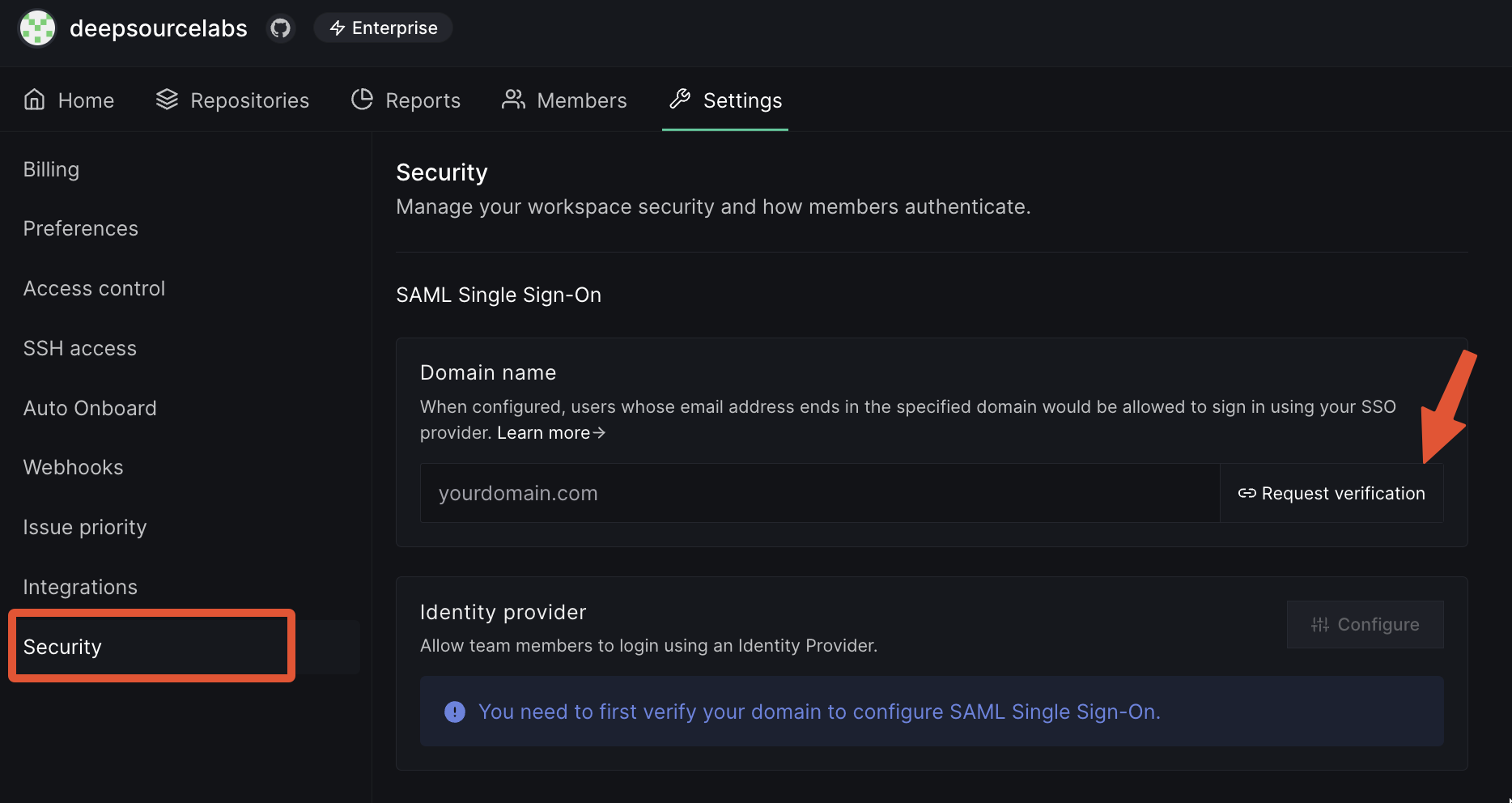
- Click on Request Verification.
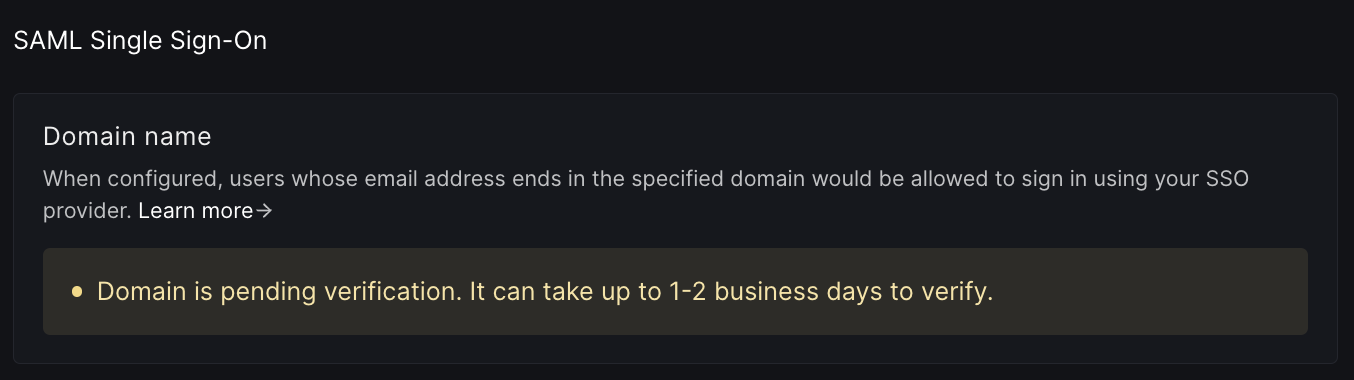
- We will reach out to you by email for a manual verification.
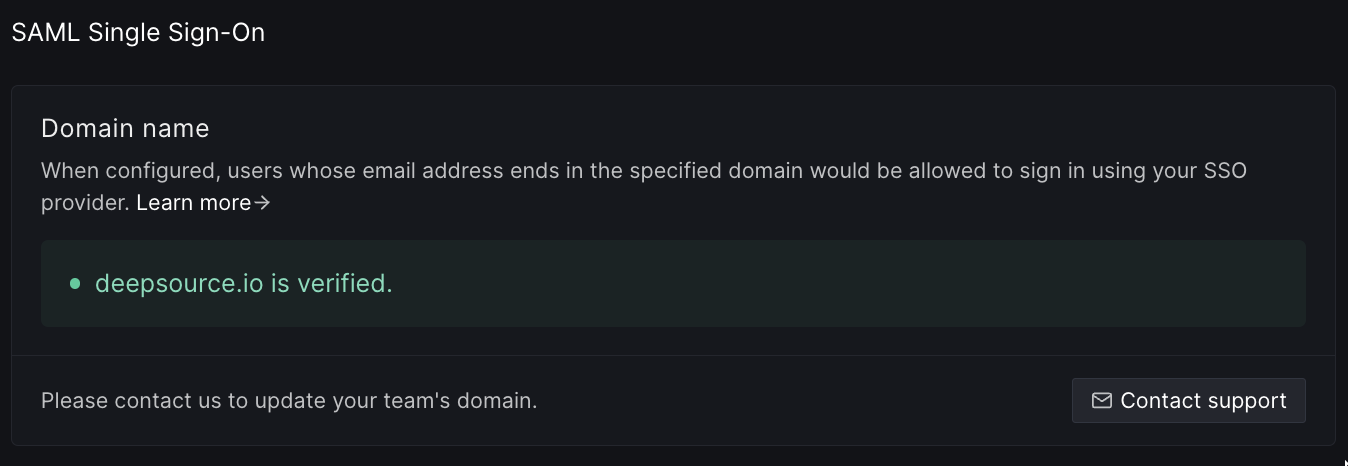
- Once your domain has been verified, you can go ahead with configuring an identity provider.
Add Identity Provider
Once DeepSource has verified your domain and you have successfully created and tested a SAML 2.0 connector on the IdP website, you need to tell DeepSource about it.- On the same Team settings -> Security page, click on the Configure button.
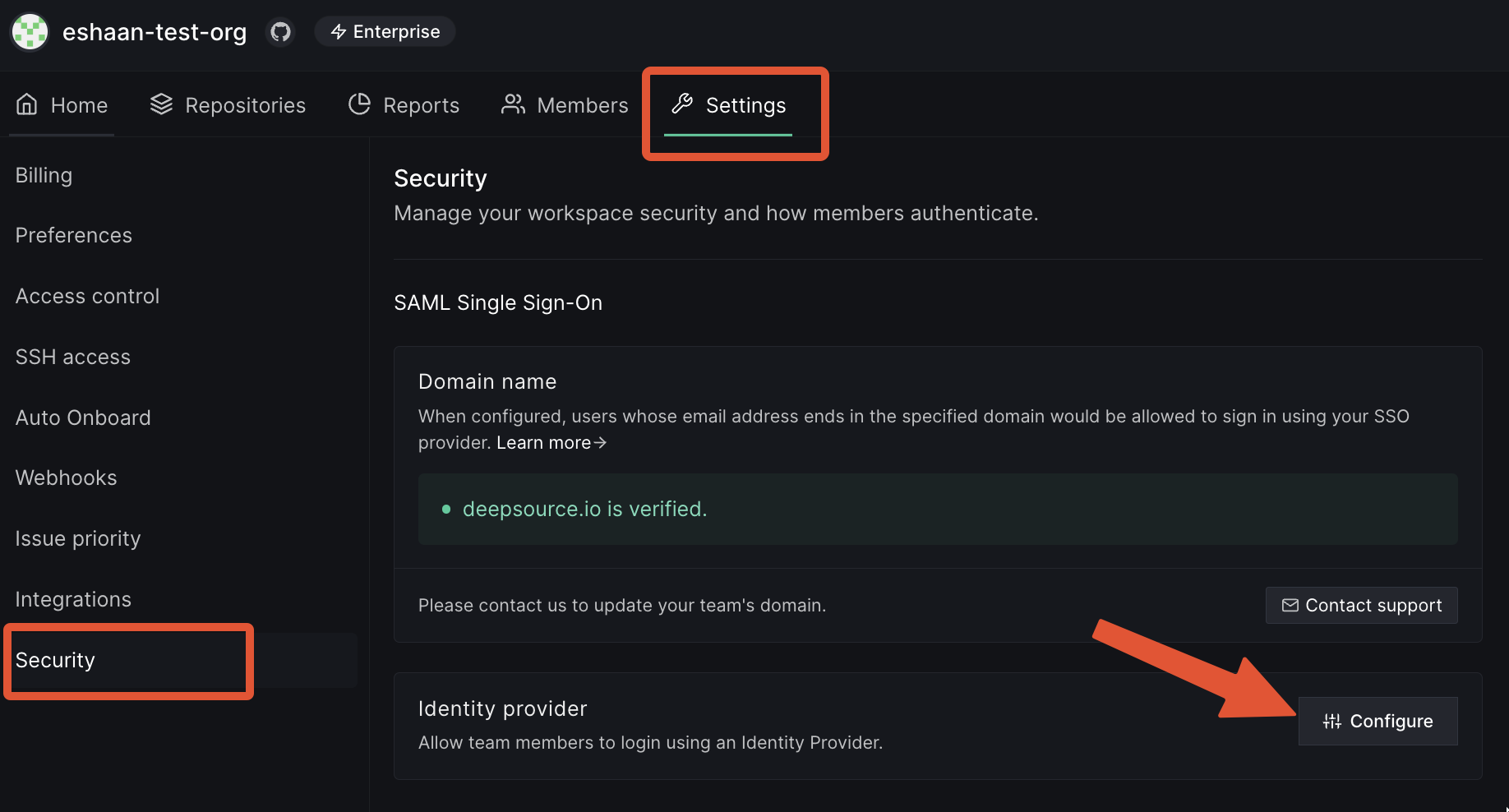
- Enter the XML Metadata URL (aka Issuer URL) that you got from the SAML connector in the IdP.
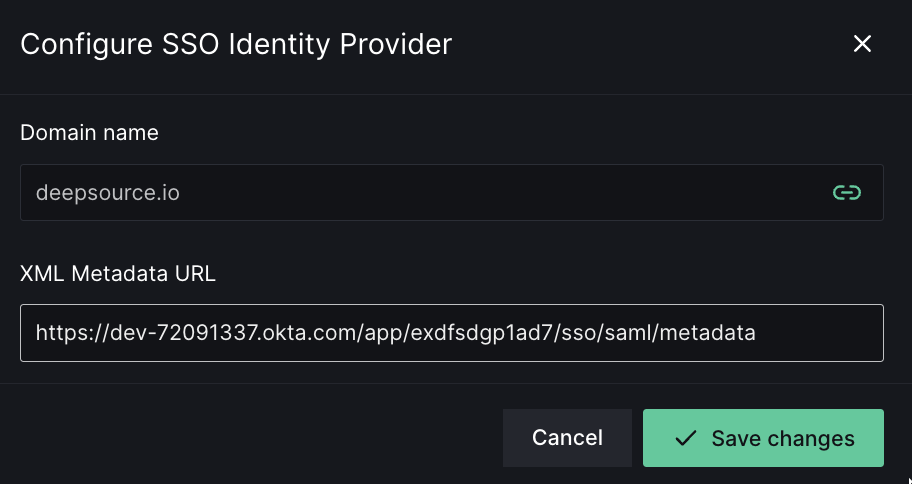
- Click on Save changes.
- Your IdP is successfully connected with your DeepSource team now. This means users assigned to the app on IdP will be able to sign up or sign in to DeepSource with SAML SSO now.
If you have enabled SAML and not SCIM, then users are provisioned access to your team Just-In-Time i.e. when the user signs into DeepSource with SAML SSO using your team’s configured IdP. They are given the
MEMBER role if there are empty seats else CONTRIBUTOR role.Configuration on DeepSource Enterprise Server
Once SAML has been configured on your IdP, navigate to “Config” tab in the Kotsadm admin panel:- Check “Yes” for “Enable SAML SSO”.
- Enter the XML Metadata URL copied above for “IdP metadata URL”.
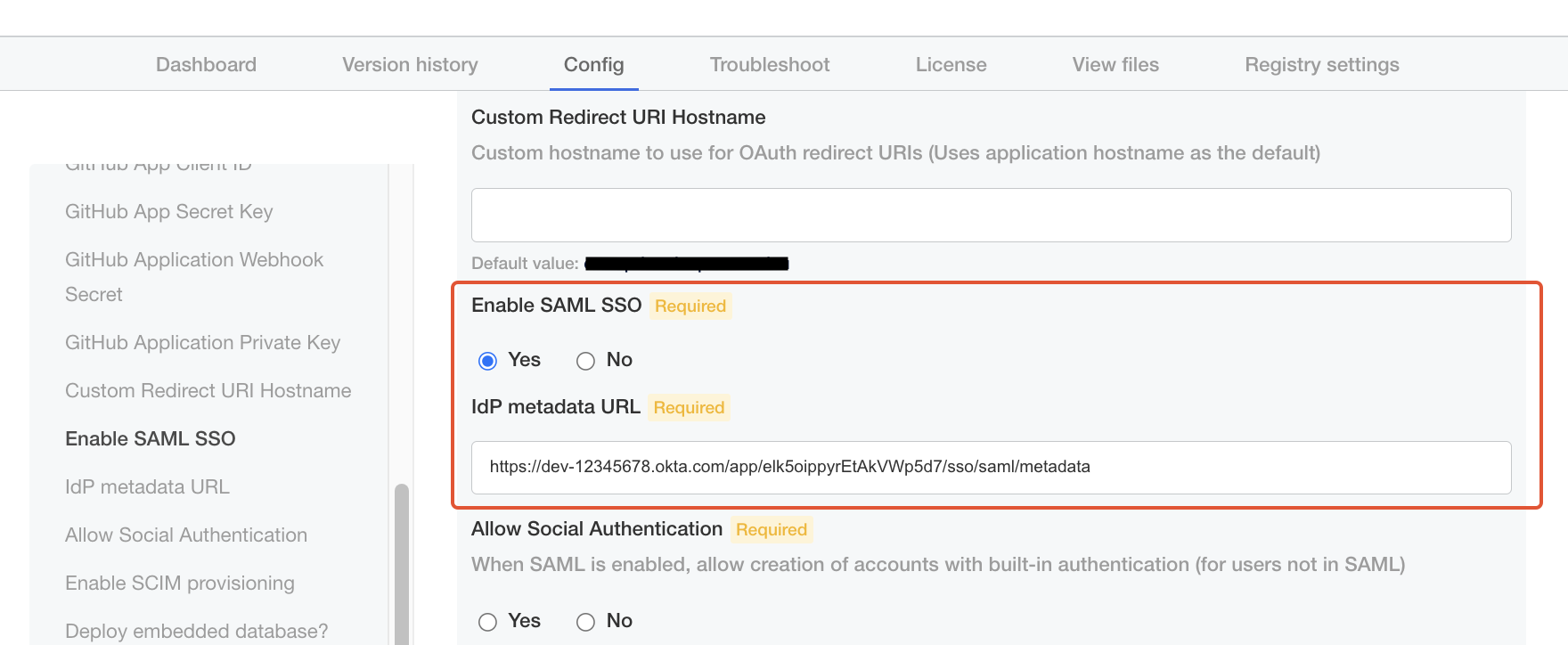
- One last piece of configuration is whether you want to enable social authentication (i.e. allowing users to be created/log in with GitHub) alongside SAML. In this case, users will be allowed to either sign in via SSO or via OAuth. Choose accordingly.
- Click save, and deploy the new version. You should now be able to Sign in to DeepSource Enterprise with SAML SSO.
Setup SCIM Provisioning
SCIM, or System for Cross-domain Identity Management, is an open standard that allows for the automation of user provisioning. With SCIM enabled for your DeepSource team, users will be provisioned, updated, and de-provisioned in real-time with respect to changes on the IdP.Configuration on DeepSource Enterprise Cloud
Once you have setup SAML SSO, you can optionally enable SCIM provisioning as well.- Go to the same Team settings -> Security page.
- Enable the toggle labeled “SCIM provisioning”.
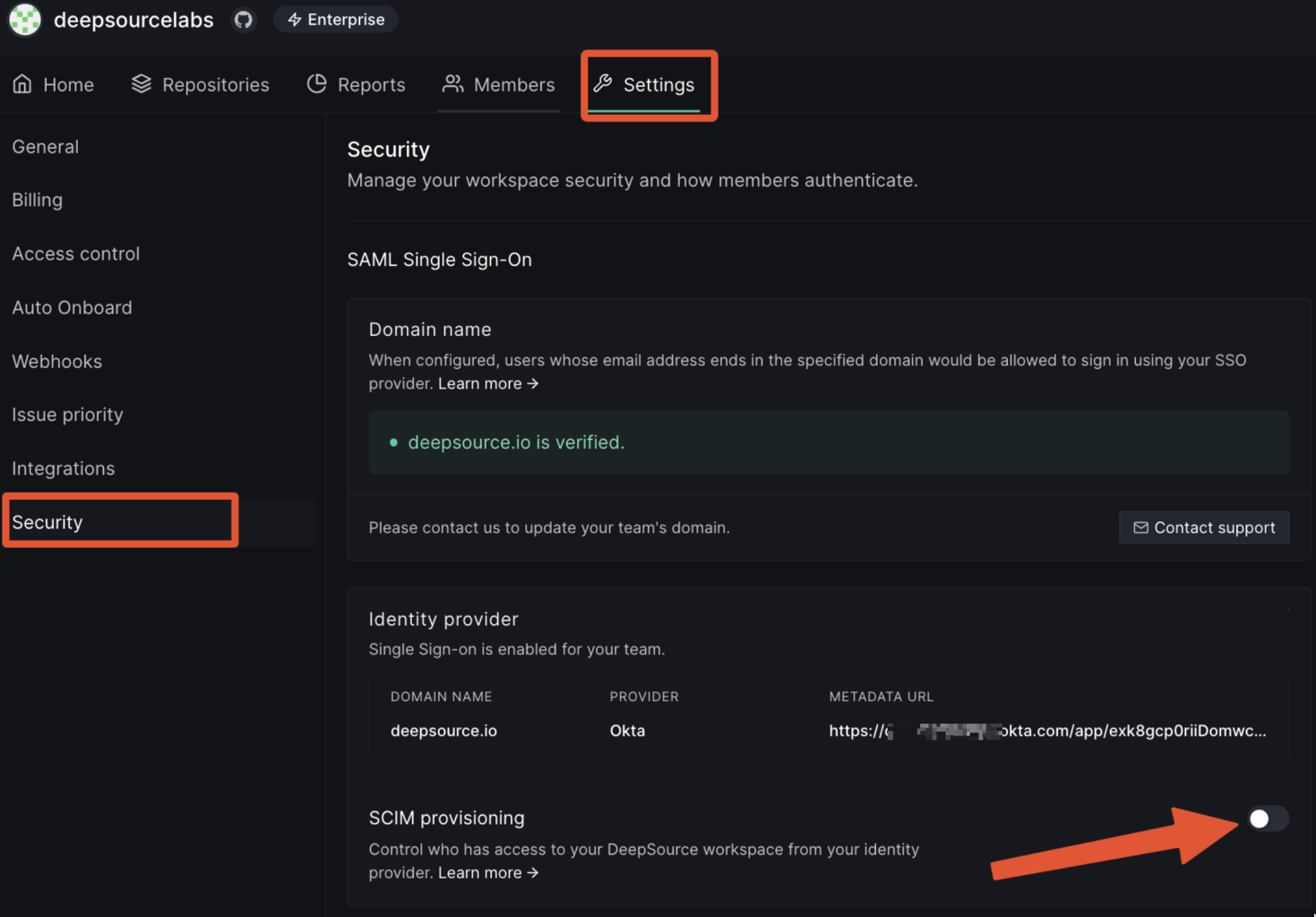
- When you toggle it, a modal will pop up displaying the SCIM authentication token. You should copy the token and dismiss the modal.
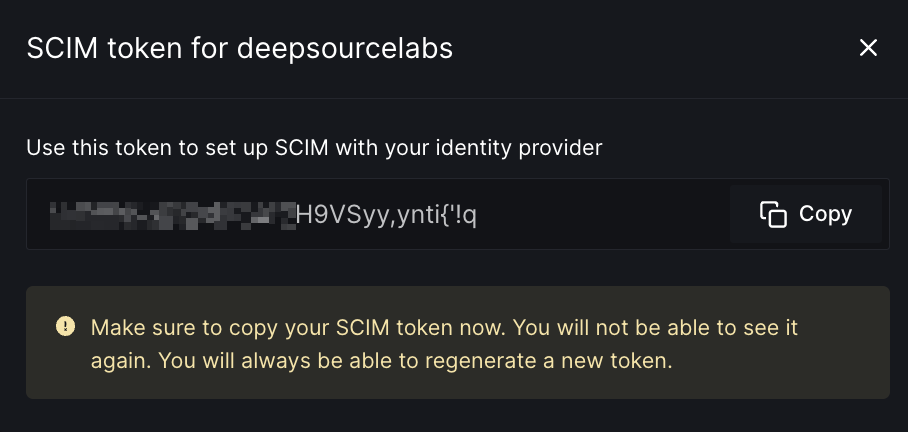
- Now SCIM is enabled for your DeepSource team. You may click on the “Regenerate” button at any time to reset the SCIM token.
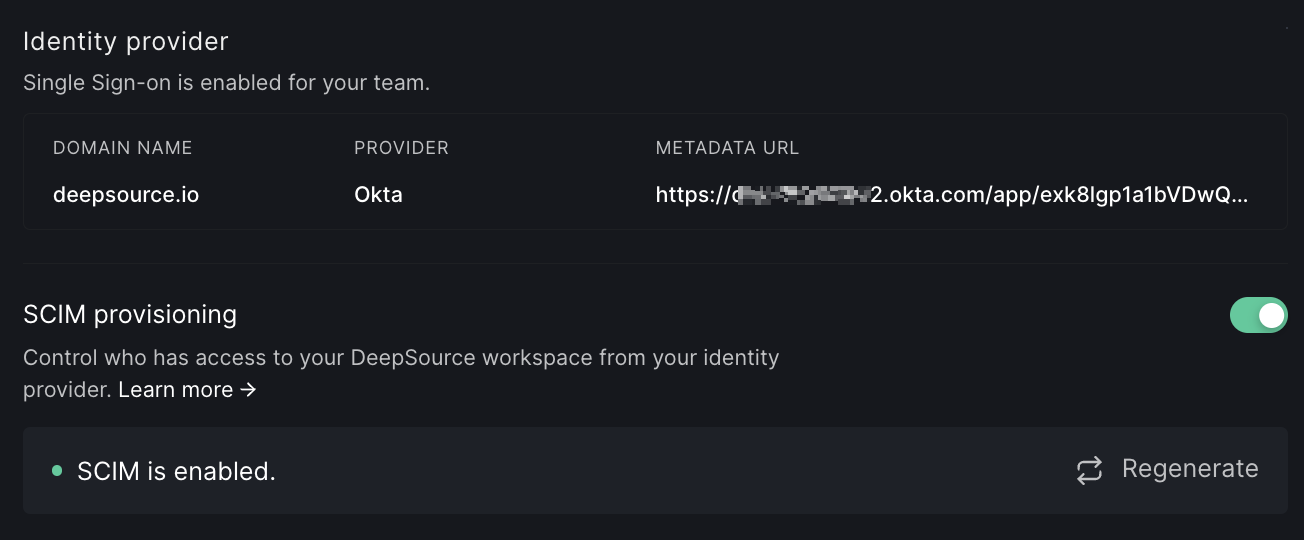
- You can go ahead with configuring and testing the SCIM connection on your identity provider. You can find the configuration steps in the “SCIM Provisioning” section for the identity provider chosen in the Configuration on Identity Provider section.
Configuration on DeepSource Enterprise Server
Navigate to “Config” tab in the Kotsadm admin panel:- Check “Yes” for “Enable SCIM provisioning”.
- Enter a strong secret of your choice in “SCIM Authentication token”. Keep this token saved somewhere, you will need to enter this in your IdP while setting up SCIM provisioning.
- Click “Save”, and deploy the new version.