Policies
Policies lets you configure DeepSource for your team, from a single place.
AI Policy
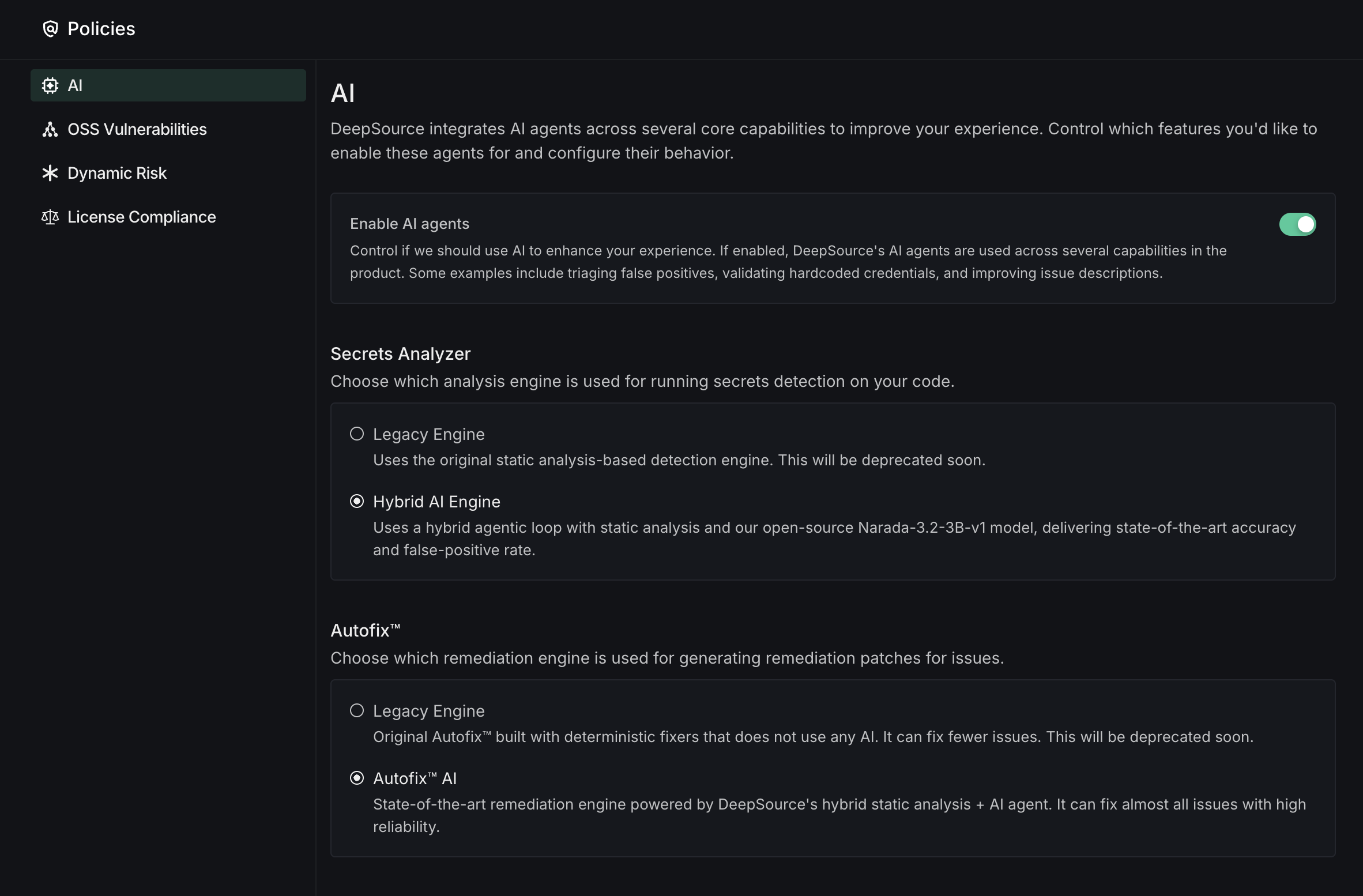
The AI Policy section lets you configure AI-powered features for your team. These settings apply to all repositories in your team.
-
AI Agents: Master toggle to enable or disable all AI-powered features globally. When disabled, all AI settings below cannot be modified.
-
Secrets Analyzer Engine: Choose the detection engine for the Secrets Analyzer:
- Legacy Engine: Static analysis-based detection. This engine will be deprecated.
- Hybrid AI Agent: Agentic loop with static analysis, powered by Narada-3.2-3B-v1. Delivers state-of-the-art accuracy with industry-leading false-positive rate. (Recommended)
-
Autofix™ Engine: Choose the remediation engine for Autofix:
- Legacy Autofix: Deterministic rule-based fixers. This engine will be deprecated.
- Autofix AI: LLM-powered remediation that can fix almost all detected issues. (Recommended)
AI Policy settings are available on all plans on DeepSource Cloud. We currently do not support this on DeepSource Enterprise Server.
SCA Vulnerabilities
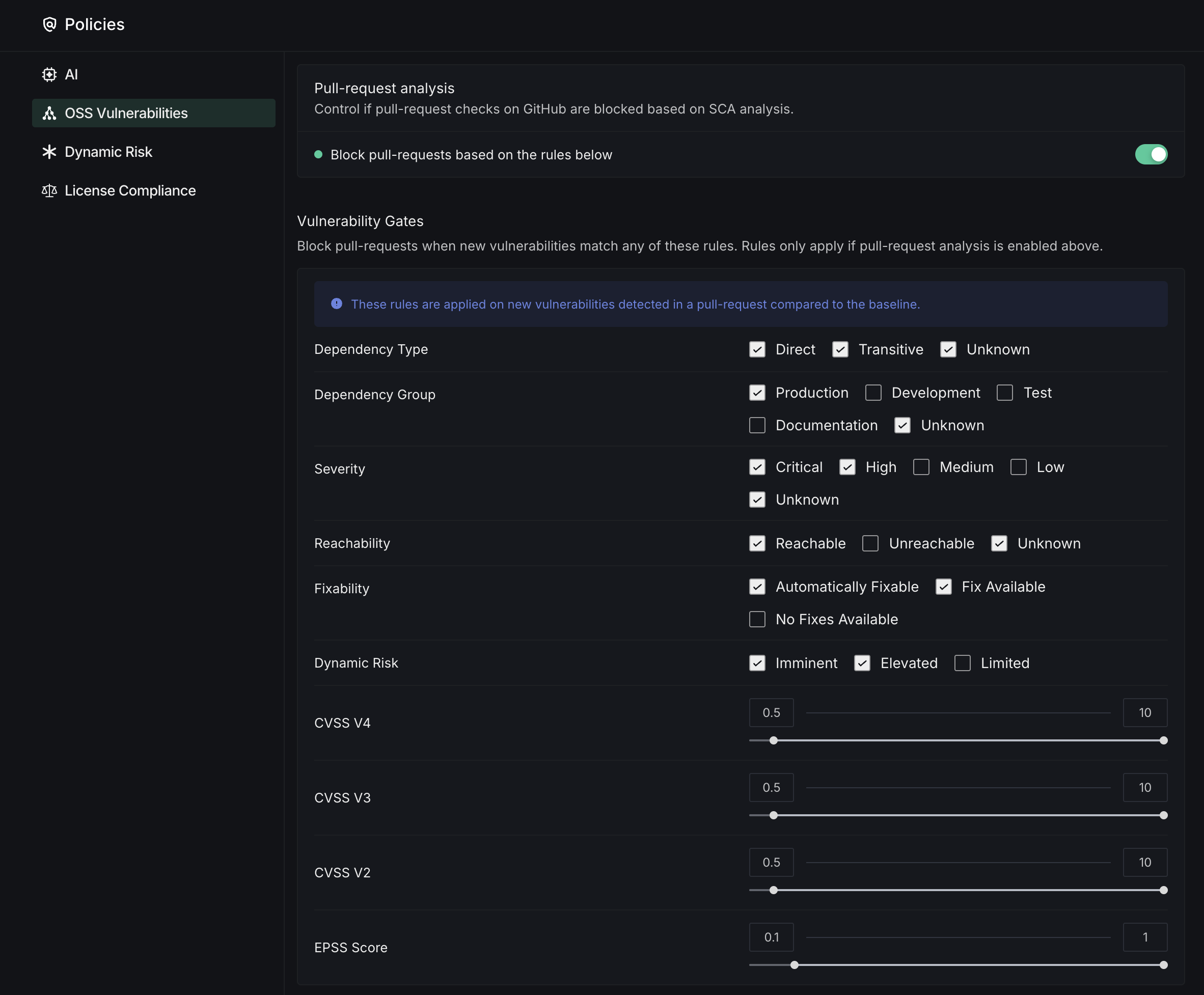
The Pull-request analysis section lets you configure how vulnerability findings affect your GitHub workflows.
- Block Pull-Requests: Toggle to enable automatic blocking of pull requests based on configured vulnerability rules
- Dependency Filtering: Select which dependencies to monitor by type (Direct, Transitive), environment (Production, Development, Test), and documentation
- Severity Controls: Choose which severity levels (Critical, High, Medium, Low) will trigger blocking
- Reachability Options: Filter vulnerabilities based on whether they're directly accessible in your code
- Fixability Settings: Control blocking based on whether automated fixes are available for detected issues
- CVSS Score Thresholds: Set minimum score requirements for different CVSS versions (V2, V3, V4) and EPSS using sliding scales
Dynamic Risk
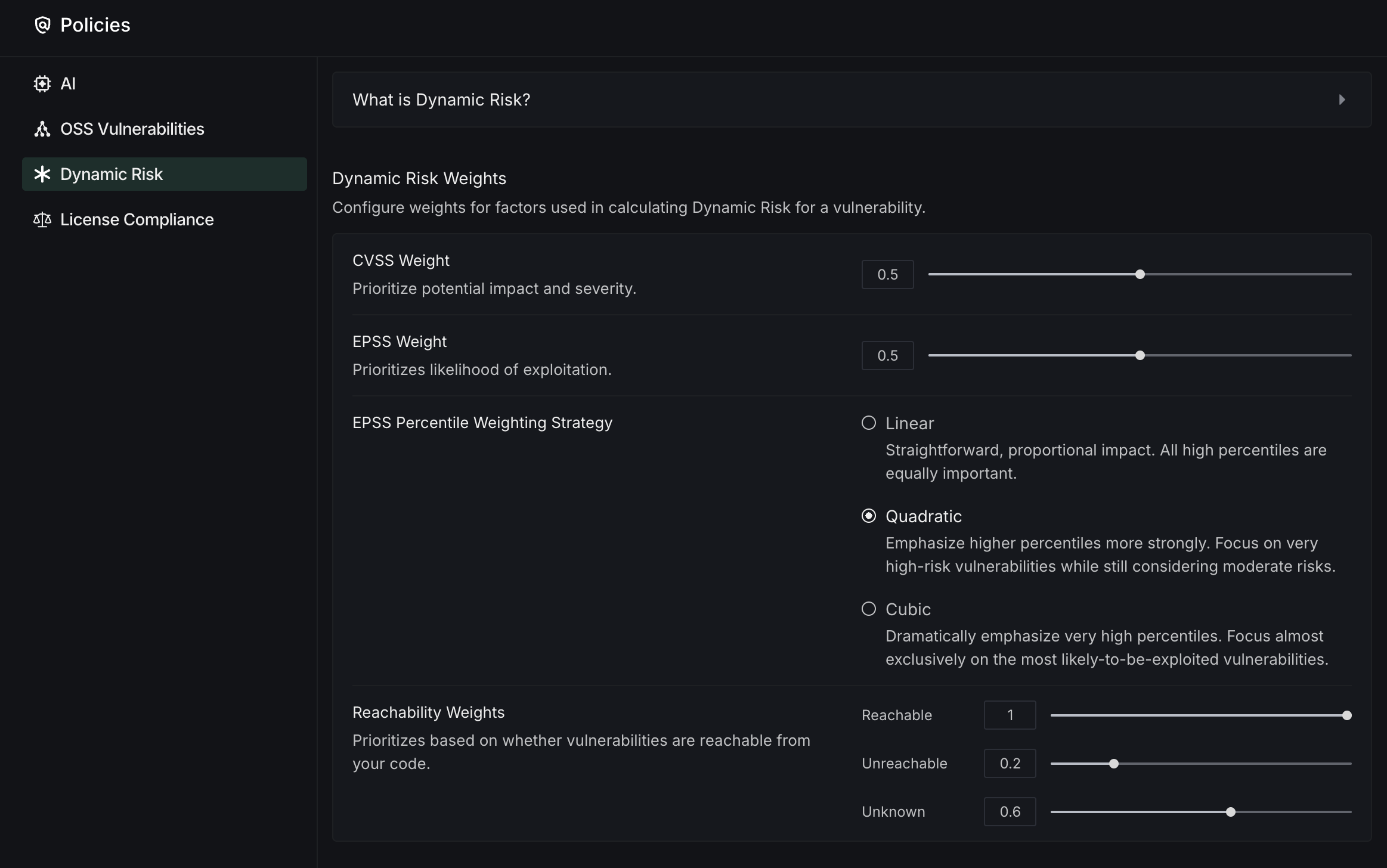
Dynamic Risk is DeepSource's custom vulnerability metric that combines CVSS, EPSS, and reachability analysis into a single, actionable score. This comprehensive assessment helps security teams prioritize vulnerabilities based on real-world impact and allocate resources more effectively. Configure how DeepSource prioritizes vulnerabilities based on multiple risk factors.
- Risk Weighting System: Adjust weights for factors used in calculating Dynamic Risk scores:
- CVSS Weight: Prioritize based on vulnerability impact and severity
- EPSS Weight: Prioritize based on exploitation likelihood
- Reachability Weights: Assign importance to whether vulnerabilities are accessible from your code
- Weighting Strategy: Choose how EPSS percentiles are calculated:
- Linear: Equal importance to all high percentiles
- Quadratic: Greater emphasis on very high-risk vulnerabilities
- Cubic: Almost exclusive focus on the most likely-to-be-exploited vulnerabilities
License Compliance
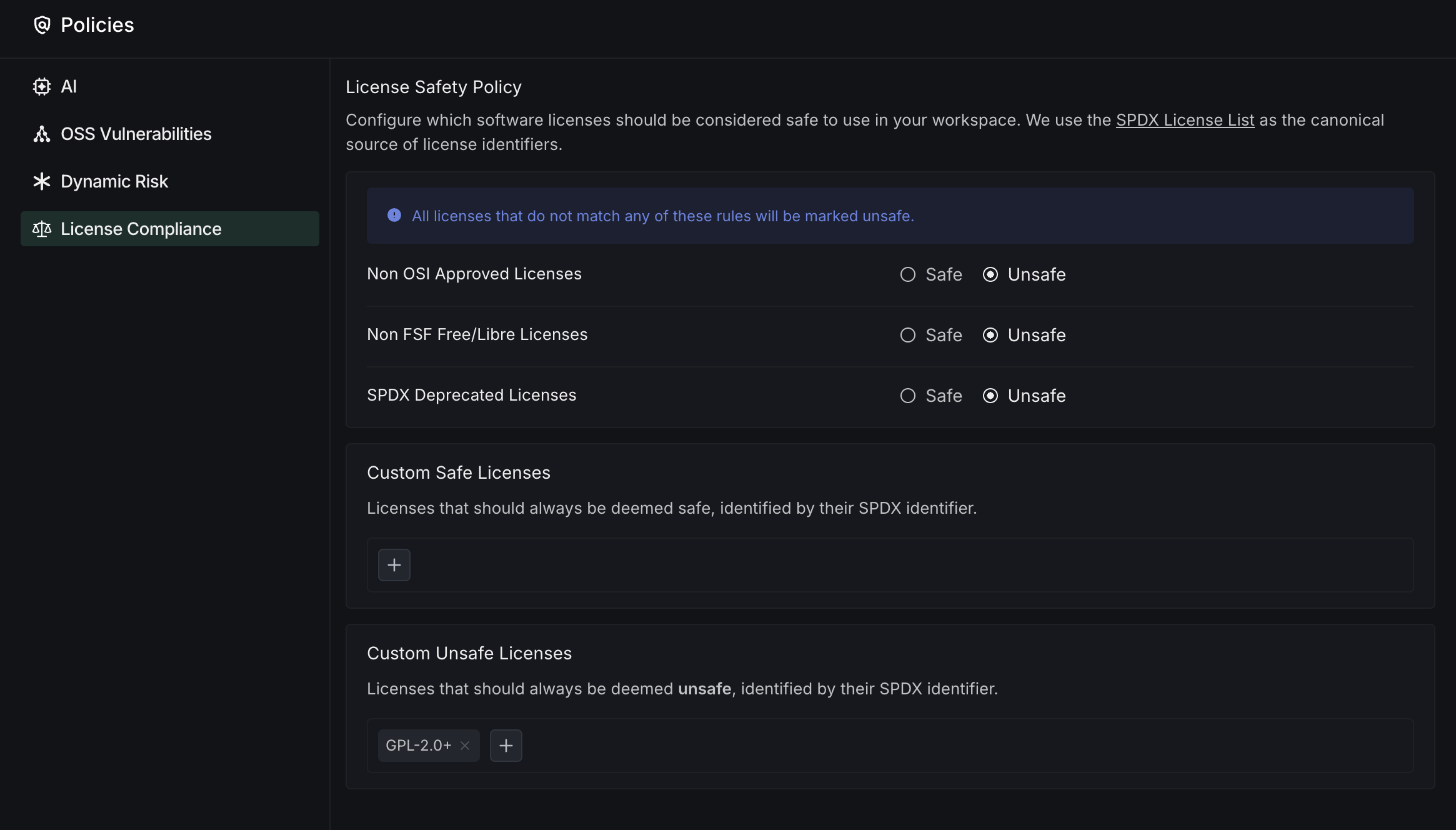
The License Compliance section lets you configure which software licenses are considered safe to use in your team. This helps your team maintain compliance with organizational license policies and reduces legal risks.
- License Safety Policy: Define which categories of licenses are acceptable for your team
- SPDX License List: DeepSource uses the SPDX License List as the canonical source for license identifiers
- License Category Rules: Set policies for different license categories:
- Non OSI Approved Licenses: Mark licenses not approved by the Open Source Initiative as safe or unsafe
- Non FSF Free/Libre Licenses: Control usage of licenses not recognized by the Free Software Foundation
- SPDX Deprecated Licenses: Manage the use of licenses that have been deprecated in the SPDX standard
- Custom License Lists: Create and manage custom rules for specific licenses
- Custom Safe Licenses: Add specific SPDX identifiers that should always be deemed safe
- Custom Unsafe Licenses: Add specific SPDX identifiers that should always be deemed unsafe
This configuration helps your team avoid introducing dependencies with licenses that don't align with your organization's legal requirements or open source policies.