Dependencies
The Dependencies tab provides a comprehensive overview of all dependencies used in your codebase, including their versions and licenses. It also highlights any vulnerabilities associated with these dependencies.
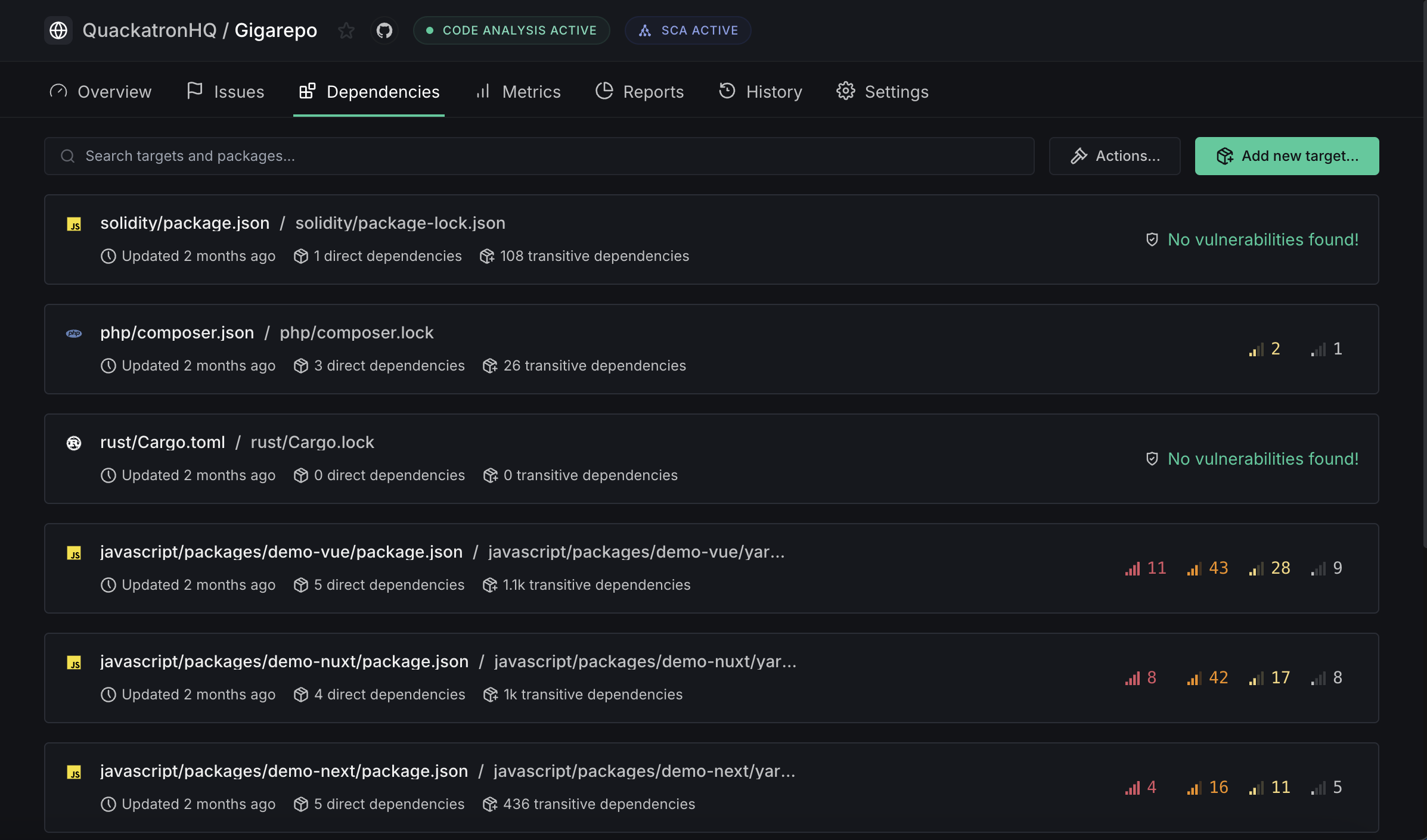
This central dashboard helps you manage security risks and dependency health with the following capabilities:
- Monitor dependency health and security vulnerabilities
- Track package versions and licenses
- Identify vulnerable dependencies with severity ratings
- Analyze reachability of vulnerabilities within your code
- View direct and transitive dependency relationships
- Prioritize fixes using Dynamic Risk Score
- Apply one-click fixes for supported vulnerabilities
List of supported targets can be found here.
Actions [1] currently has the option to automatically discover and sync all targets in a repository.
Add a new target [2] enables you to manually register a dependency manifest file for scanning. By selecting your package manager (such as Python's requirements.txt), specifying the path to your manifest file (like package.json or pyproject.toml), and optionally adding the corresponding lock file path, you can quickly add new dependency manifest files (targets) into the dashboard.
Vulnerabilities
The Vulnerabilities section displays detected security vulnerabilities for each target. This view shows both direct and transitive dependency vulnerabilities, with CVE identifiers and affected package information.
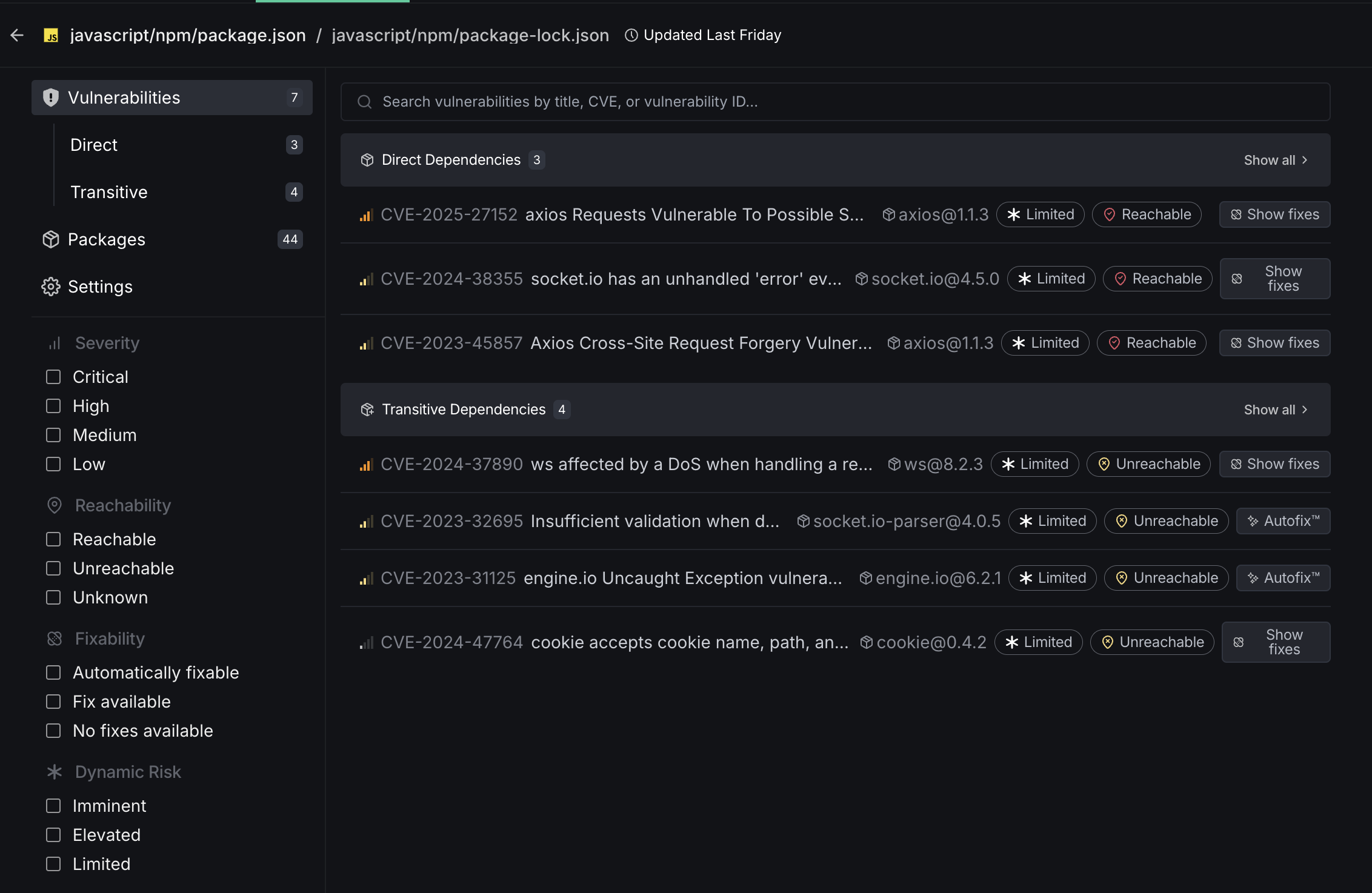
-
Severity: Sort vulnerabilities by Critical, High, Medium, or Low severity to prioritize remediation efforts.
-
Reachability: Identify whether vulnerable code is actually called by your application code. This distinguishes between theoretical vulnerabilities and those that pose genuine risk by analyzing your call graph to determine if vulnerable functions are reachable through execution paths.
-
Fixability: View available fixes, patch versions, and leverage one-click Autofix™ capabilities for supported packages.
-
Dynamic Risk Score: DeepSource's custom vulnerability metric that combines CVSS, EPSS, and reachability analysis into a single, actionable score. This comprehensive assessment helps security teams prioritize vulnerabilities based on real-world impact and allocate resources more effectively.
Packages
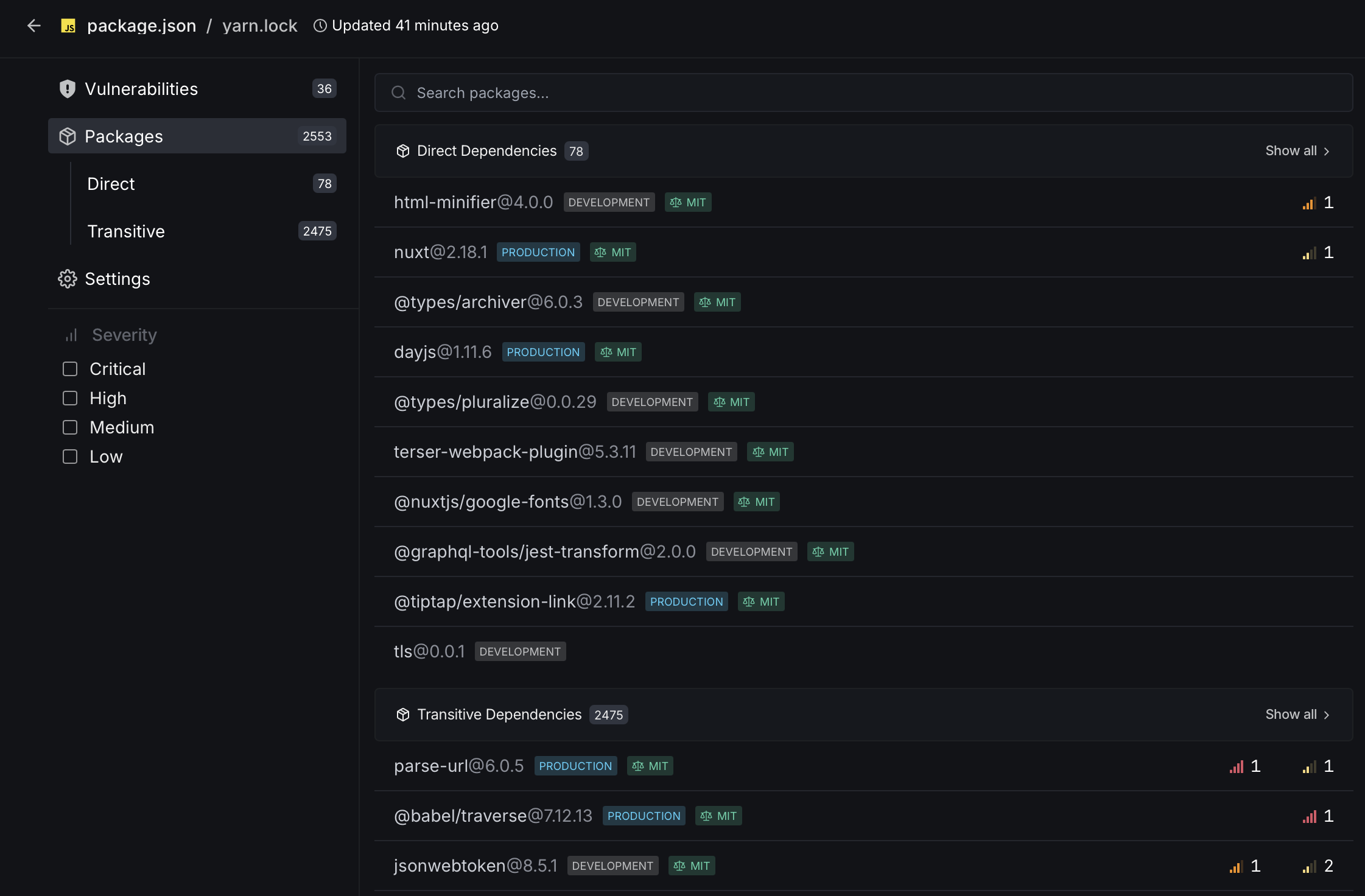
The Packages section lists all dependencies used in your project, organized by direct and transitive dependencies. This view provides visibility into your dependency structure, showing package names, versions, and potential issues.
- Direct Dependencies: Lists immediate dependencies explicitly declared in your package manifest, showing version information and production status.
- Transitive Dependencies: Shows nested dependencies pulled in by your direct dependencies, helping you understand your complete dependency tree.
- Version Information: Each package displays its current version with a label indicating its environment (Production, Development, etc.).
- License Information: Displays the license type for each package, helping you ensure compliance with open-source licenses. Refer to the Policies section to enforce license compliance.
- Metrics Indicators: Small bars next to packages indicate vulnerability count with it's severity related to each dependency.
- Filtering & Search: Quickly locate specific packages using the search functionality or filter by dependency type.
- Package Details: Click on any package to view additional information, usage details, and potential upgrade paths.
Settings
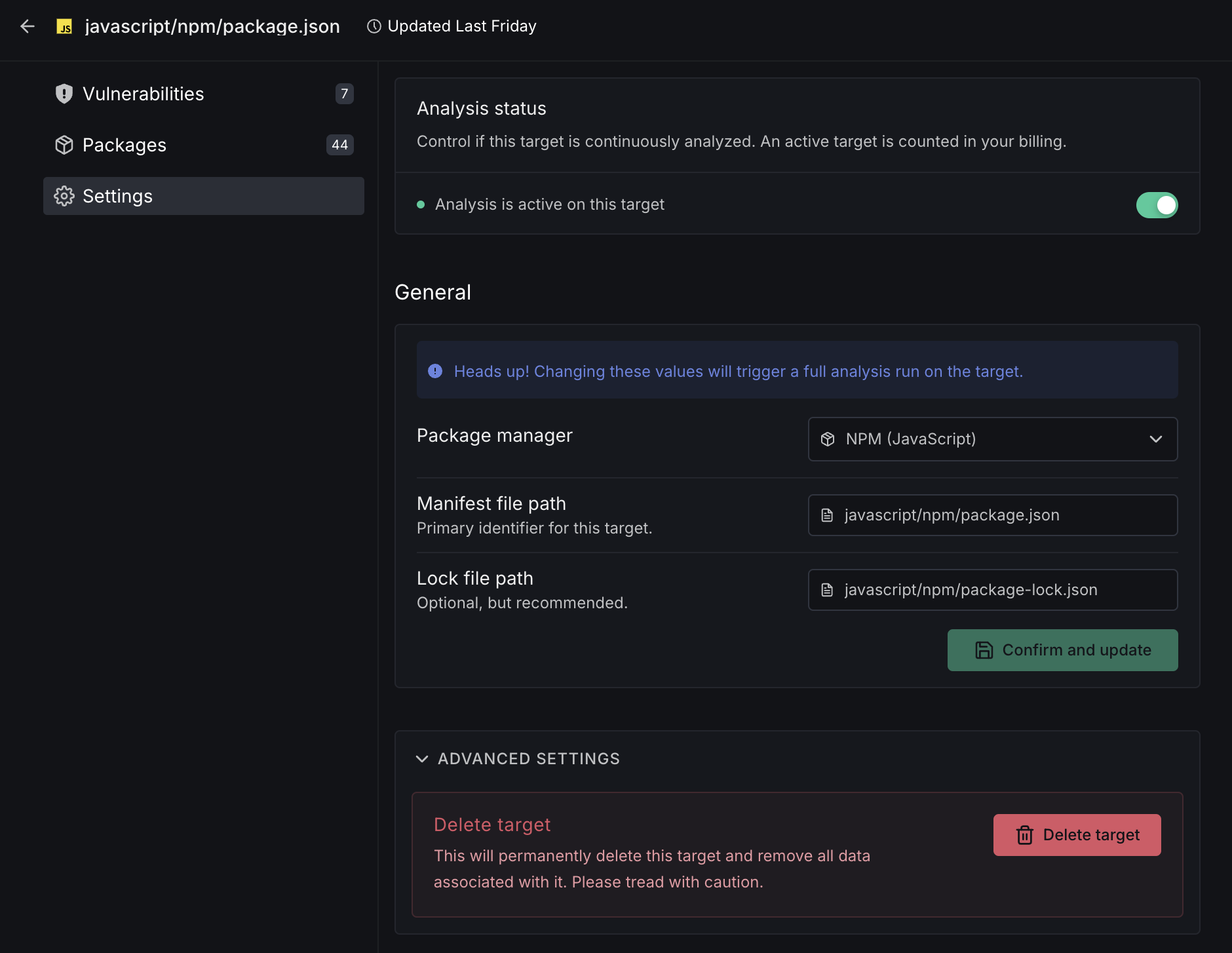
The Settings section allows you to configure how your dependency target is monitored and analyzed. This view provides options to control analysis status and adjust target configuration.
-
Analysis Status: Toggle whether this target is actively being analyzed. Active targets are included in your billing and continuously monitored for vulnerabilities.
-
General Settings: Configure the core properties of your dependency target:
- Package manager selection (NPM, Yarn, Pip, etc.)
- Manifest file path defining the primary location of your dependency declarations
- Lock file path for more precise dependency resolution (optional but recommended)
-
Advanced Settings: Access additional configuration options, including the ability to delete a target.
Vulnerability
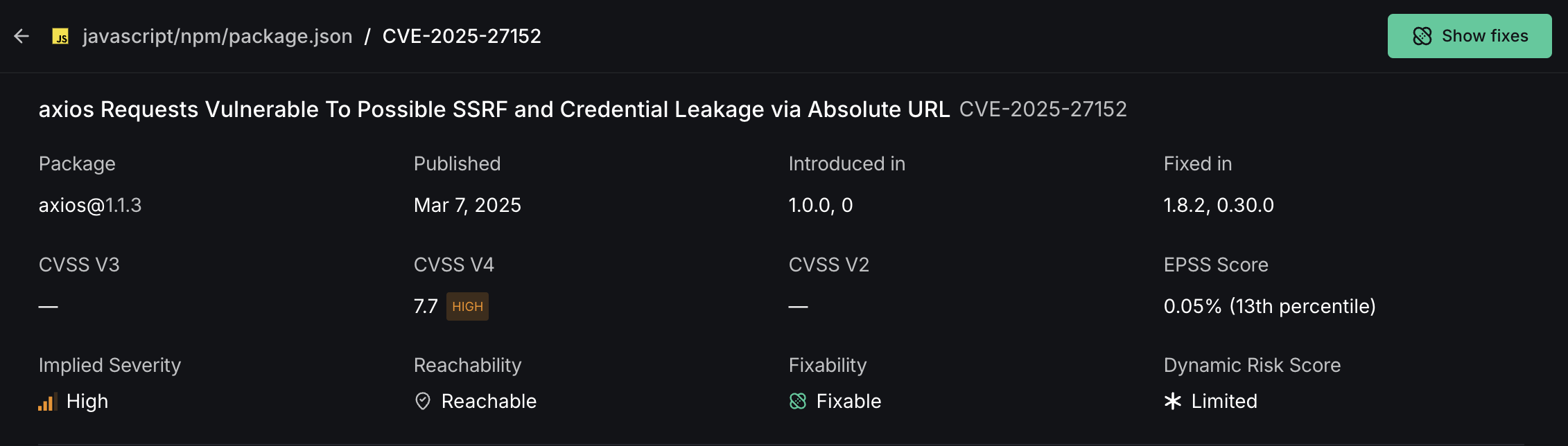
Overview
The Vulnerability Overview section provides detailed information about a specific security vulnerability detected in your dependencies. This comprehensive view helps you understand the risk, impact, and remediation options.
- Vulnerability Title and CVE: Displays the full name of the vulnerability and its unique CVE identifier
- Affected Package: Shows which package contains the vulnerability and its specific version
- Timeline Information: Includes when the vulnerability was published, which version introduced it, and which version contains the fix
- Severity Metrics: Presents multiple scoring systems (CVSS V3/V4/V2) to help assess the severity of the vulnerability
- EPSS Score: Shows the Exploit Prediction Scoring System percentage, indicating the likelihood of exploitation
- Actionable Insights: Provides reachability status (whether vulnerable code is called by your application), fixability options, and an overall Dynamic Risk Score.
- Remediation: Access available fixes via the "Show fixes" button to resolve the vulnerability
Dynamic Risk Score is DeepSource's custom vulnerability metric that combines CVSS, EPSS, and reachability analysis into a single, actionable score. This comprehensive assessment helps security teams prioritize vulnerabilities based on real-world impact and allocate resources more effectively.
Reachable Call Graphs
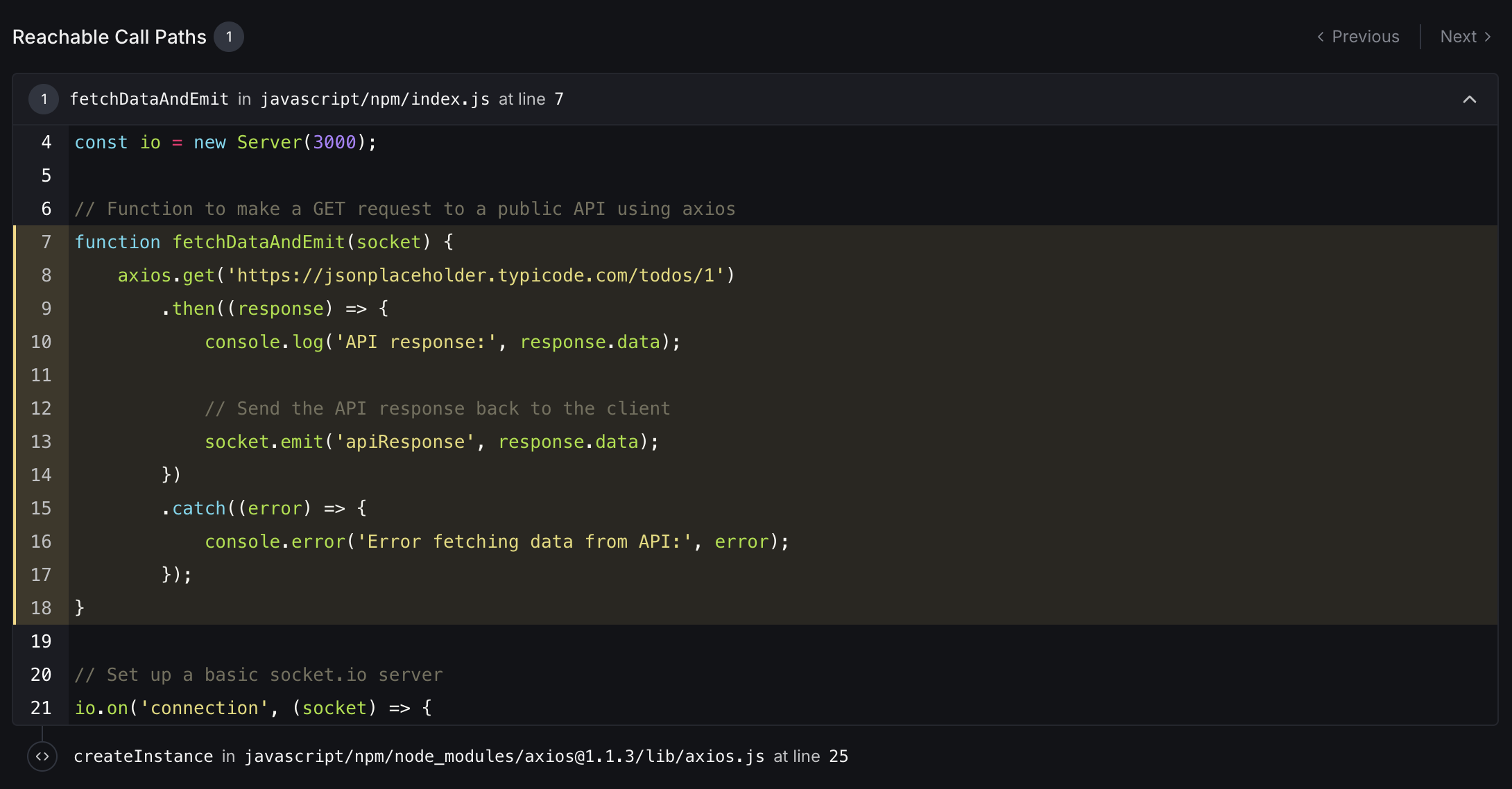
The Reachable Call Paths section shows how vulnerable code can be executed in your application. This view displays the actual code paths that could trigger the security vulnerability.
- Path Navigation: Browse through different vulnerable execution paths with Previous/Next controls
- Function Trace: Shows the function call chain from your application code to the vulnerable dependency
- Code Context: Displays the relevant source code with line numbers and syntax highlighting
- Vulnerability Location: Highlights exactly where the vulnerable code is being called
- Call Stack: Shows both your application code and the internal library code that creates the vulnerability
- File References: Includes file paths and line numbers for precise vulnerability location
This information helps developers understand exactly how a vulnerability could be exploited in their specific application context, making remediation efforts more targeted and effective.
The 'Description' section provides a detailed explanation of the vulnerability, including its impact and potential consequences along with reference URLs.
Fixing a Vulnerability
When a security vulnerability is detected in your project dependencies, you can resolve it using one of two approaches: Autofix (when available) or manual fix. This guide explains both options.
Autofix
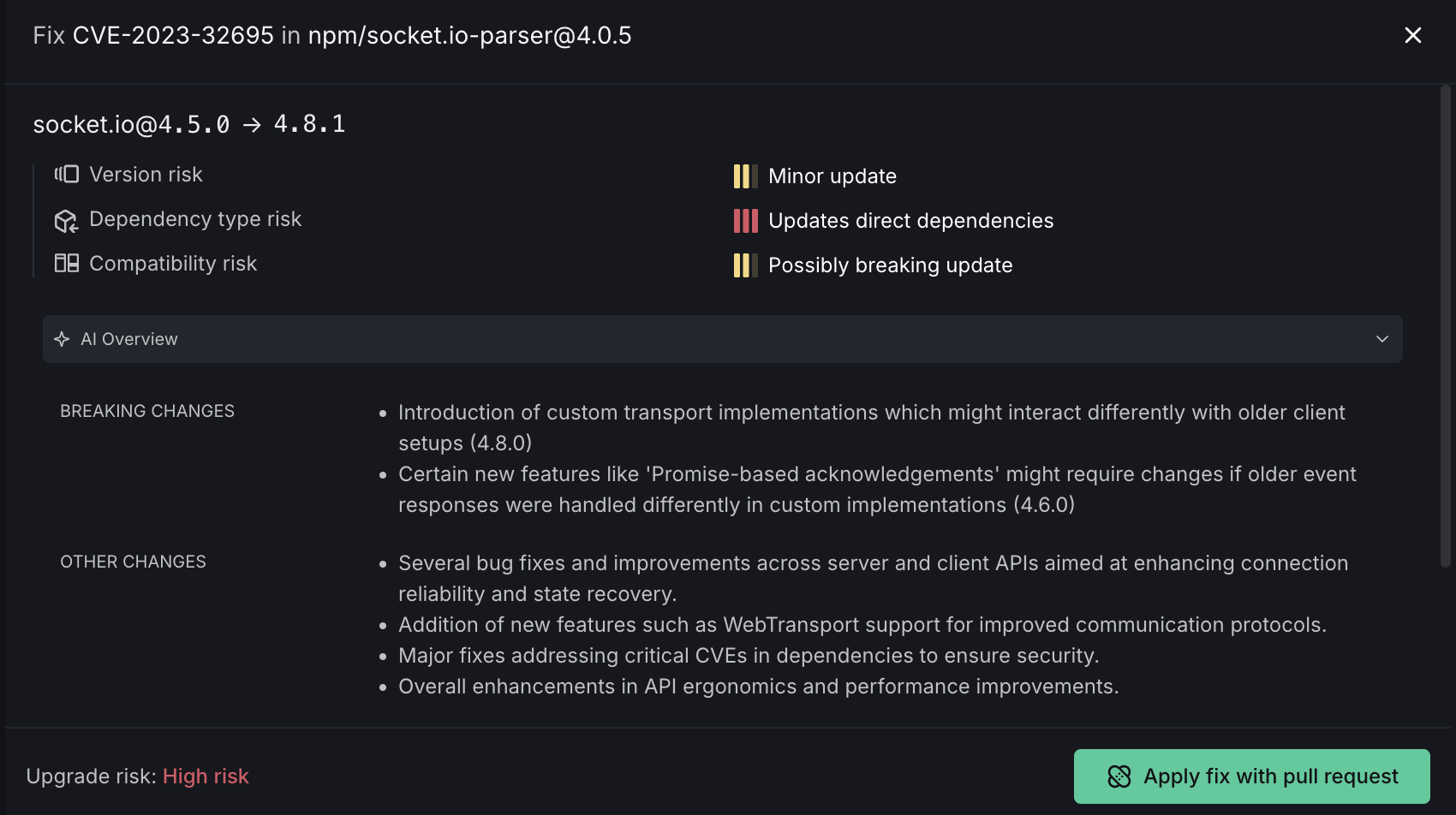
The Autofix option allows you to quickly resolve vulnerabilities through an automated pull request. The interface provides:
- Package Upgrade Information: Shows the vulnerable package (e.g., socket.io@4.5.0) and the target fixed version (e.g., 4.8.1)
- Risk Assessment:
- Version risk indicator
- Dependency type risk
- Compatibility risk
- Update classification (Minor update, Updates direct dependencies, Possibly breaking update)
- AI Overview: AI Overview provides information about the fix, to help developers assess the safety and impact of upgrading third-party dependencies in their projects. It uses an agentic loop under the hood to gather information about different versions of a package and shows the user a summary of changes, as well as a breakage score that indicates the likelihood of breaking changes.
Once reviewed, click "Apply fix with pull request" to automatically create a PR with the necessary changes.
Manual Fix
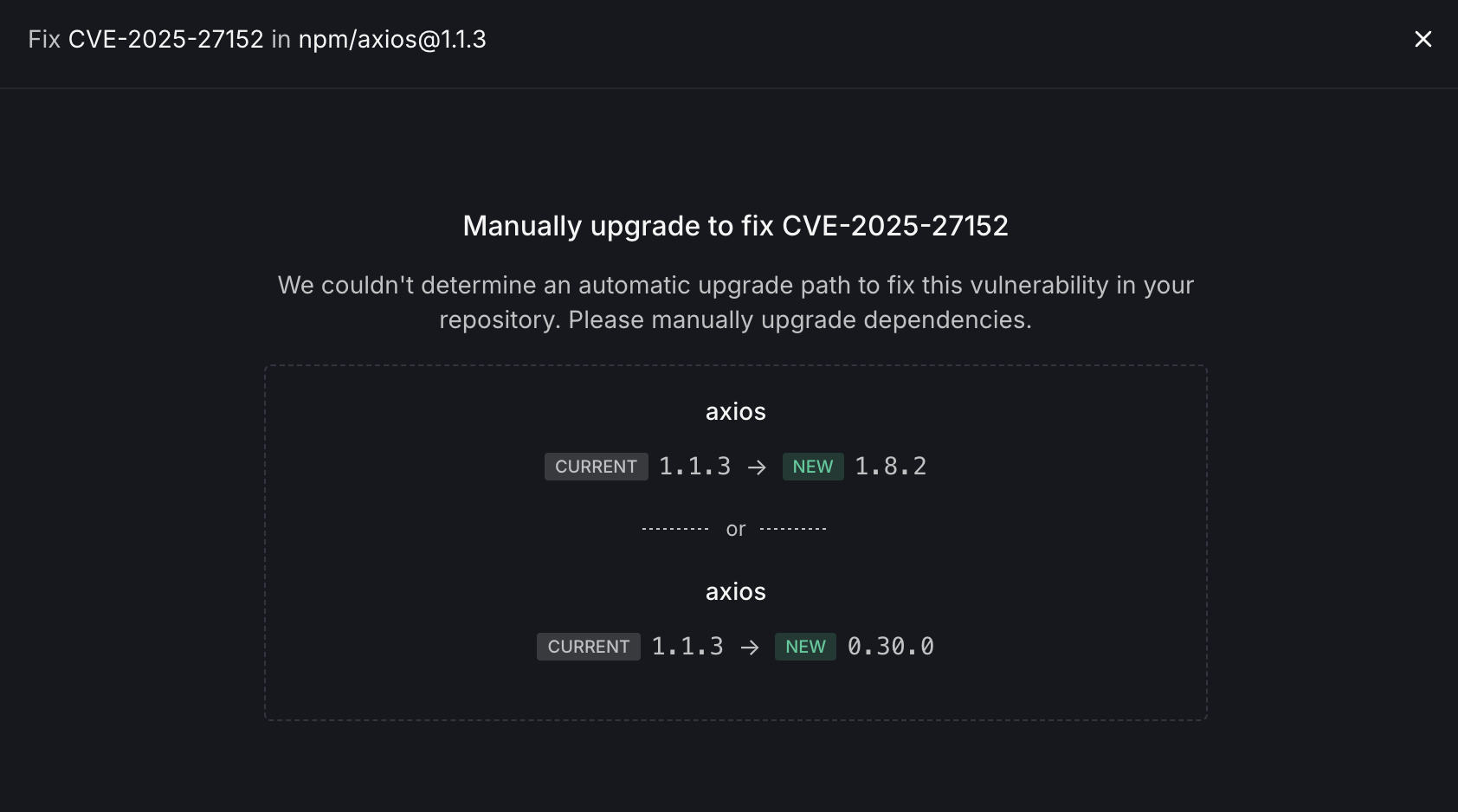
When Autofix isn't available, you'll need to manually upgrade your dependencies. This happens when an automatic upgrade path couldn't be determined for your repository.
- Package Information: Identifies the vulnerable package (e.g., axios@1.1.3)
- Upgrade Options: Presents multiple potential upgrade paths:
- Option 1: Upgrade to a newer version in the same major version line (e.g., 1.1.3 → 1.8.2)
- Option 2: Consider alternative versions that may involve more significant changes (e.g., 1.1.3 → 0.30.0)
After identifying the appropriate upgrade path, you'll need to manually update your target file and run your respective package manager's command to apply the changes.
Best Practices for Fixing Vulnerabilities
- Review the changes: Before applying any fix, understand the potential impact on your codebase
- Test thoroughly: After upgrading, run your test suite to ensure compatibility
- Check for breaking changes: Pay special attention to major version upgrades which are more likely to contain breaking changes
- Consider dependency impact: Be aware that upgrading one package might affect other dependencies
- Maintain documentation: Record significant dependency upgrades in your project changelog